Interdependent Privacy
The notion of privacy is a collective concern [1]. So when studying privacy or designing new technologies, it is essential to consider this social construct to better protect individuals’ privacy. Recent reviews on privacy scrutinized the social aspect of privacy by proposing new notions called ‘interdependent privacy’ [2,3] or ‘privacy dependencies’ [4]. These studies explain how our privacy depends on the decisions of other people including our partners, families, friends, colleagues, and strangers in society.
A paper by Barocas and Levy published in Washington Law Review [4] provides a framework explaining three different ways that our privacy might get disclosed一caused by other individuals.
(1) Tie-based Dependency
Tie-based dependency explains (i) how an observer (e.g., 3rd party service provider or government) can collect information about us if a friend or family member knowingly or unknowingly disclose that information, (ii) how one’s information can be accidentally caught (e.g., bystanders), (iii) how one’s identity can be revealed by information from her acquaintance (e.g., family members sharing similar genetic patterns), or (iv) how one’s connection with others can help to collect information about others (e.g., contact chaining or Cambridge Analytica examples).
(2) Similarity-based Dependency
Similarity-based dependency explains how the following situations can help for inference of information or identity (i) being a member of the same family or sharing the same house, (ii) belonging to the same socially salient groups (age, gender, religion), or (iii) showing similar behaviors like using the same webpage, buying the same product, etc.
(3) Difference-based Dependency
Difference-based dependency is about finding the required information about a person based on her/his differences from others which including three approaches: (i) elimination which means that if someone discloses her information, this can make her distinguishable from others and finally can reveal other’s information or identity (ii) detecting those whose behavior or data are abnormal (iii) detecting those that trying to hide information or impede the observer, e.g., if everyone routinely discloses tax information, those who avoid such behavior might be the suspicious cases.
Intimate Privacy
Considering the sensitivity of the disclosed information, the severity of the privacy conflicts, and its negative consequences on individuals can differ. One of the situations that severe consequences might occur is privacy conflicts in intimate relationships. Partners usually access a lot of information from each other that disclosure of such information can threaten peer privacy and can finally hurt the peer. Partners could disclose such information with different motivations [5]. Most of the time, emotional reasons play a critical role, when partners want to retaliate against their peer after their relationship ended up (e.g., revenge pornography). Partners could also use such privacy threats to gain personal benefits, for example, to prolong a one-sided relationship.
Another form of privacy violation in intimate relationships is intimate monitoring. While such surveillance could be useful in some types of relations (e.g., parental control), monitoring an adult person in partnership relations might have painful repercussions for the person who is under surveillance.
Intimate Partner Surveillance (IPS)
A recent study [6] showed that online communities such as public ‘relationship infidelity forums’ can serve perpetrators (i.e., those who monitor their partner) as a platform to discuss the techniques and tools required for IPS (e.g., how to use a keylogger to hack the partners’ password). Nevertheless, it is yet unclear why perpetrators are interested in IPS and what are their motivations for seeking information related to IPS on such websites.
A CSCW paper [7] by Bellini and colleagues studied IPS by analyzing comments left by perpetrators on three different online forums. The study used a mixed-method research approach where it first used a narrative analysis method to understand justifications and motivations provided by perpetrators for IPS and second it used a grounded theory approach to create a conceptual framework to better understand perpetrators’ attitude changes during the IPS procedure.
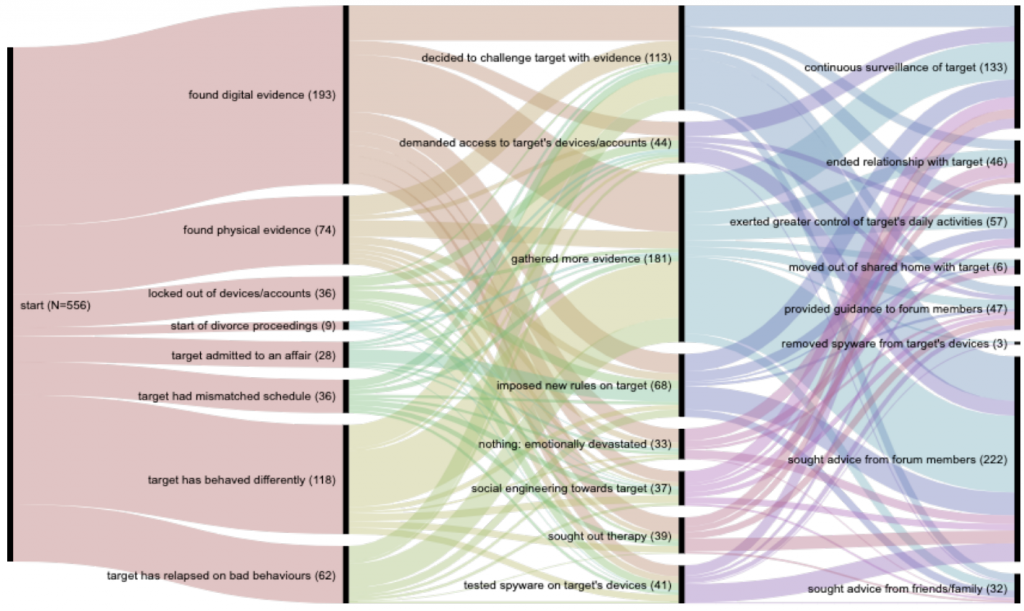
By analyzing 556 posts through three different forums, authors found a chronological structure consisting of three different acts related to IPS. Figure 1 shows these three steps including setup (i.e., the reasons incentivized IPS for example if their partner started behaving differently), confrontation (i.e. the initial actions that perpetrators did in response by gathering more evidence), and resolution (i.e., the actions they did to solve the issue by seeking advice from the forum members).
Figure 1. Three main actions related to IPS
The perpetrators used different justifications in their posts to commit IPS including
- to make sure their partner is being faithful
- to gather evidence discovering the partner betrayal
- to understand the reasons behind sudden behavior changes
- to control their partners’ devices or social media accounts.
While committing IPS, perpetrators often disclose different types of information about themselves and their partners including their physical spaces (workplace, holiday destination, home) and digital spaces (work devices, printed records, phone). They also give gender information about themselves, their partner, and a third party person (e.g., an affair partner). Disclosure of such information can create an opportunity for adversaries such as cyber attackers.
The paper also showed that perpetrators use such forums to
- request help and guidance from others, e.g., “any suggestions for installing spyware”.
- to help others how to commit IPS, e.g., “keep snooping!”
- to support and validate others by sharing similar experiences, e.g., “this is too dramatic!”
- to praise themselves for the IPS they committed before, e.g., “I told him I was watching his every move!”
- to monitor and gatekeep newcomers in the forum, e.g., “you should first share your story here before asking for answers!”
In the second part of the paper, the authors used grounded theory to provide a conceptual framework on how perpetrators change their attitudes during the IPS process. For this purpose, they used open coding, axial coding, and selective coding to analyze data systematically. The outcome is shown in Figure 2, and it includes four main stages: setting expectations, change in attitude, escalation, and reflection.
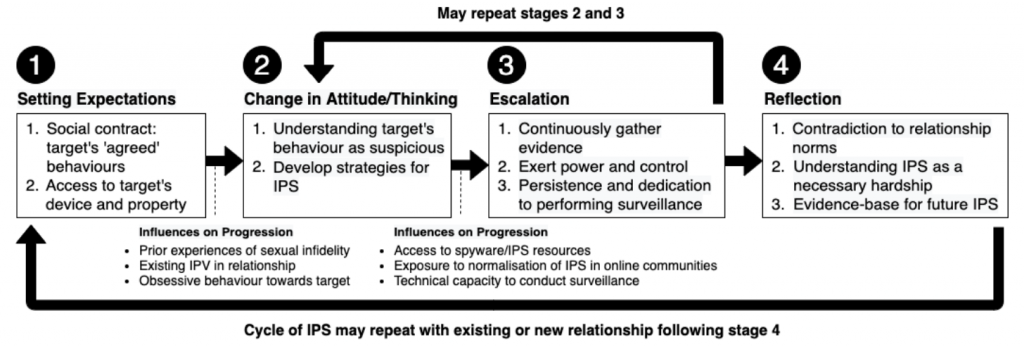
Figure 2. A conceptual framework for attitude changes in IPS
According to this framework, perpetrators expect certain behavioral standards from their partners to demonstrate their trust based on their social contract (either implicit contract, e.g., promise, or explicit contract, e.g., a marriage contract). Based on this trust relationship perpetrators expect to have open access to all information of their partners. When perpetrators could not make sure of this trust relationship or when they noticed any suspicious change in their partner behavior, they start to change their attitude by using different wordings or by committing the first IPS actions. Perpetrators may escalate their IPS actions by looking for more techniques and tools and to increase the surveillance or they may reduce if they become confident about their relationships or if they do not have enough technical capacity to expand their surveillance. Last, only those perpetrators who stop the surveillance might reflect on their actions. Such reflections could make perpetrators realize that they indeed violated their own personal values, e.g., trust, and then deleting the gathered evidence!
The paper discusses different implications of the findings on how to make online forums safer environments and to make interventions to protect partners’ privacy against surveillance. (For further information please click here!)
Author: Kavous SALEHZADEH NIKSIRAT
References
- Petronio, S. Communication Privacy Management Theory: What Do We Know About Family Privacy Regulation? J. Fam. Theory Rev. 2, 175–196 (2010).
https://doi.org/10.1111/j.1756-2589.2010.00052.x
- Humbert, M. & Huguenin, K. Interdependent Privacy. in Encyclopedia of Cryptography, Security and Privacy 5 (2020).
https://hal.archives-ouvertes.fr/hal-02523728/
- Humbert, M., Trubert, B. & Huguenin, K. A Survey on Interdependent Privacy. ACM Comput. Surv. 52, 122:1–122:40 (2019).
https://doi.org/10.1145/3360498
- Barocas, S. & Levy, K. Privacy Dependencies. (2019).
https://papers.ssrn.com/abstract=3447384
- Levy, K. & Schneier, B. Privacy threats in intimate relationships. J. Cybersecurity 6, (2020).
https://academic.oup.com/cybersecurity/article/6/1/tyaa006/5849222
- Tseng, E. et al. The Tools and Tactics Used in Intimate Partner Surveillance: An Analysis of Online Infidelity Forums. in 1893–1909 (2020).
https://arxiv.org/abs/2005.14341
- Bellini, R. et al. “So-called privacy breeds evil’’: Narrative Justifications for Intimate Partner Surveillance in Online Forums. J ACM 1, 27.
https://damonmccoy.com/papers/IPS_CSCW.pdf
© Thumbnail photo by Dayne Topkin on Unsplash